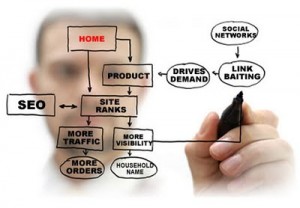
Typo 3 is not as popular a service as WordPress or Joomla but is a reliable platform that boasts many features. The program allows its users to have the best settings for managing a large amount of information through numerous internet connections. T...